
Two-factor authentication and facial recognition with Keycloak
With online safety becoming an increasing concern, the adoption of two-factor authentication is prevalent. Single passwords are no longer robust in this day and age, and so the need for a second layer of protection ensures better security of online accounts.
The commonly used two-factor authentication methods at the moment are One-Time Passwords (SMS Verification or App-Generated Codes), Tokens, RFID cards and Security Keys.
What are the common problems in using two-factor authentication?
- User will have to carry a token/device with them all the time.
- It will cost to set up two-factor authentication solution (software and hardware costs) and for maintenance as well.
- Users might lose their keys and smart cards or accidentally ruin them.
- Users must carry a mobile phone, charged, and in range of a cellular network. If the phone is unable to display messages, access is often impossible without backup plans.
- Mobile phones can be stolen, potentially allowing the thief to gain access into the user’s accounts.
- Text messages may not be delivered instantly, adding additional delays to the authentication process.
- Hackers can set up or reconfigure two-factor authentication to keep you out of your own accounts.
How are we solving this problem?
Zaizi’s implementing a step which verifies the user’s face as the second factor of authentication in Keycloak.
The advantages are:
- Simplifies access control – users look at their webcam or camera and gain access instantly. No PINs to enter or smart cards to present.
- Improves security – someone’s biometric cannot easily be duplicated, lost or stolen.
- Infrastructure – there is no need for additional equipment or infrastructure since cameras are available in laptops and mobiles
- Easy integration – you won’t need to spend additional money on hardware/ software or equipment.
- High accuracy rates.
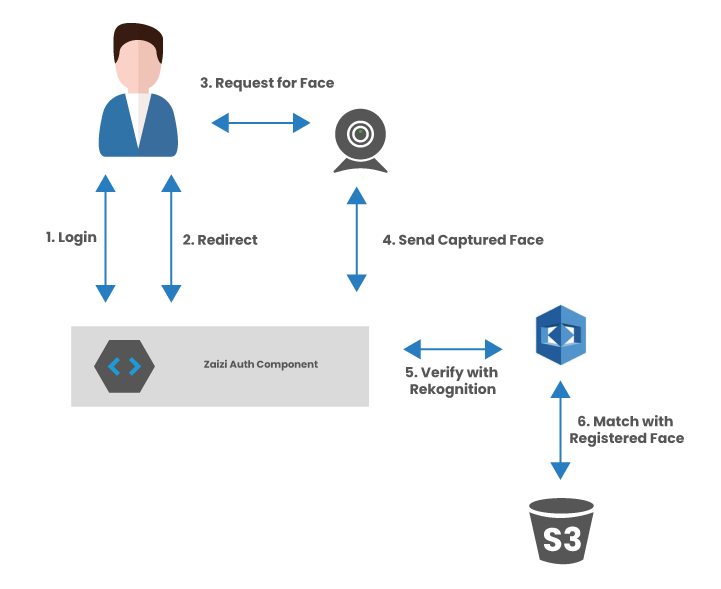
Technologies used
- Keycloak: Keycloak is an open source software that allows single sign-on with Identity Management and Access Management aimed at modern applications and services.
- AWS Rekognition: Amazon Rekognition is a simple API that can quickly analyse any image or video file stored in Amazon S3. Amazon Rekognition is always learning from new data.
- AWS S3: Amazon Simple Storage Service is used to store user images.
Summary
Two Factor authentication is the latest advancement in information security systems. It doesn’t offer absolute security (nothing can!) but it does add rigour and make your data more secure. And with face recognition capabilities, it becomes a less onerous and more user-friendly process
By The Innovation Team
Related content
-

How to design thoughtful and secure cross domain workflows
Published on: 11 June, 2024 -

What is a cross domain workflow and why does it matter?
Published on: 4 June, 2024 -

Zaizi 2023 review: Thought leadership and insights in digital government
Published on: 2 January, 2024 -

GitHub Copilot: Exploring AI pair programming tools
Published on: 15 November, 2023
